Phishing Hosting: Free web hosts continued to be favored location for hosting phishing sites, as seen on Netcraft’s Phishiest Hosters page. Also ranking highly were several hosts that seem to offer scant policing of scams, including Romanian host Home.ro/Go.ro, which was home to more than 760 phishing URLs in 2005.
More than 600 phishing spoof sites were hosted on compromised forums and content management systems, offering a reminder that security problems with these programs extend beyond the site’s operators and users. Of the phishing sites confirmed by Netcraft, 131 urls contained the phrase “phpbb,” 254 contained “forum” and 265 contained “board.”
The Geography of Phishing: A review of 5,000 of the most recently confirmed phishing URLs shows that .com continues to be the most popular top-level doman (TLD), with Russia and Romania being the only country-specific TLDs with more than 1 percent of URLs. Here’s the breakdown:
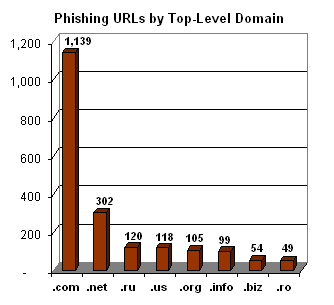
Romania has hosted 1,397 phishing sites in 2005, equivalent to about 3.3 percent of all hostnames in that country. Only South Korea (3,807 phishing URLs, or 9.1 percent of all sites) hosts a higher percentage of phishing URLs, with Taiwan (1,276, 3.0 percent) close behind. Additional detail on the geography of phishing can be found at Netcraft’s Phishiest Countries page.
The Netcraft Toolbar Community is digital neighborhood watch scheme, in which the most alert and expert members act to defend the larger community of users against phishing frauds. Once the first recipients of a phishing mail have reported the target URL, it is blocked for toolbar users who subsequently access the URL. Widely disseminated attacks (people constructing phishing attacks send literally millions of electronic mails in the expectation that some will reach customers of the bank) simply mean that the phishing attack will be reported and blocked sooner.
The Phishing Site Feed is also available to ISPs and Enterprises who wish to protect their customers or employees against phishing. Netcraft also offers services to detect open redirects on corproate web sites to prevent abuse, and fraud detection and phishing site countermeasure services.