Netcraft’s toolbar community has reported an increase in the deployment of malicious scripts which direct webmail and online banking traffic through rogue proxy servers. These proxies allow attackers to steal usernames and passwords when forms are submitted, or use victims’ cookies to hijack already-authenticated sessions.
The attacks rely on malicious proxy auto-config (PAC) scripts, which are remotely hosted and instruct a victim’s web browser to proxy certain requests according to the specified configuration. Other requests are left untouched and end up being transmitted directly to the intended websites. The selective behaviour could perhaps be an attempt to limit the amount of traffic an attacker would need to process to extract sensitive information; alternatively, it could be an attempt to make detection more difficult — the results from services such as whatismyip.com may not be indicative of whether or not traffic was being intercepted.
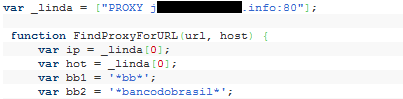
The PAC script shown above defines a JavaScript function – FindProxyForURL(url, host) – which is called by the browser. The full implementation of this function lets the attacker specify which URLs or hostnames should be requested directly, and which should be proxied. In the above example, requests to Banco do Brasil’s website will be transmitted via the attacker’s proxy server.
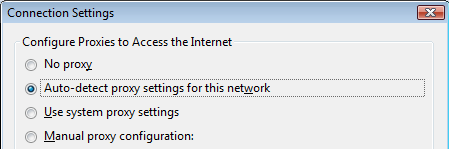
By using the Web Proxy Autodiscovery Protocol, a correctly positioned attacker could plausibly trick victims into using his phishing proxy without their knowledge. Although this feature is not enabled by default, many corporate environments may enable it in order to reduce the administrative overhead of manually configuring employees’ laptops and other mobile devices to use proxies. If these devices are subsequently connected to an untrusted wireless network – which is controlled by an attacker – the WPAD discovery process would provide the attacker with a mechanism through which he can introduce arbitrary proxy scripts into browsers.
Alternative methods of attack include somehow enticing users to manually edit their proxy settings (perhaps by falsely claiming that it would result in performance benefits), or manipulating the settings via malware running on the user’s computer. Similar malware-driven attacks have been around since 2008 and offer the attacker the additional advantage of being able to ensure that the malicious proxy settings cannot be tampered with.
Previous attacks using this technique originally targeted customers of Brazilian banks, but the fraudsters have since widened their scope and now also proxy traffic destined for webmail services such as Hotmail and Gmail, American banks, and one of the world’s most popular phishing targets – PayPal.
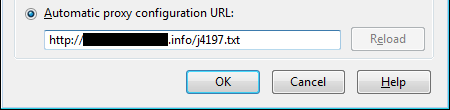
To mitigate such attacks, it would be wise to avoid using automatic proxy detection settings on untrusted networks, and to also ensure your browser’s automatic proxy configuration URL does not contain an unexpected address.